2049-10-45
A quick and dirty python zip file brute forcer - note you will need a list of possible words so you know get to OSINT
Python Script
[+]
import pyzipper
import itertools
import string
# Define character sets for generating passwords
lowercase = 'abcdefghijklmnopqrstuvwxyz' # a-z
digits = '0123456789' # 0-9
special = '!@#$%^&*()_+-=[]{}|;:,.<>?' # Special characters
# Function to generate variations of a password using character substitutions
def generate_variations(password):
variations = ['']
for char in password:
new_variations = []
for variant in variations:
new_variations.append(variant + char)
variations = new_variations
return variations
print("Hello, world!")
2049-10-18
Back to basics
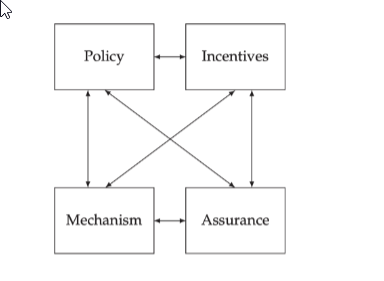

I have been doing some theory work to try to get myself more towards a real-world cyber point of view, instead of my hyper fixations.
Going through the below framework, I found it interesting to analyze the Target hack of 2013 from this perspective:
Policy - Target didn’t have policies to ensure third-party suppliers had a proper security posture. Attackers exploited a contractor’s credentials, prompting organizations to strengthen third-party risk management policies. Mechanisms - Target’s FireEye malware detection tool worked, but their incident response failed, allowing attackers to persist for weeks. Assurance - FireEye reliably detected malware, but gaps in Target’s response exposed weaknesses in their security mechanisms, such as Single Sign-On vulnerabilities. Incentives - Target was a lucrative target during the holiday shopping season. Management’s prioritization of operations over security led to delays in notifying affected customers.2049-10-15
2049-10-14
Recent finds scanning HackerOne targets.
HackerOne Profile
HackerOne Profile

